云计算中的数据安全:您的数据有多安全?
云安全领域的领导力和合作伙伴关系
定义很关键;甚至必不可少。例如,“领导力”一词在谷歌词典中被简单地定义为“领导一群人或一个组织的行为”。在phoenixNAP,行业领先是我们DNA和文化的一部分。我们将领导力定义为创造创新、可靠、成本优化和世界一流的解决方案,我们的客户可以轻松使用。
在这种情况下,术语“云基础设施”(或其前身“云计算”)往往代表多个不同的场景和解决方案,由过分热心的营销团队鼓吹。如果没有明确的定义,这些术语的清晰度充其量是令人费解的。然而,“云安全”更常被描述为代表对数据机密性、隐私、法规遵从性、恢复、灾难恢复甚至供应商生存能力的担忧。我们的目标是通过我们的数据安全云解决方案为这一领域带来清晰、明确和信任。
未来之路:安全格局
根据 Gartner 的 Heng &Kim (2016),到 2020 年,60% 的企业将遭受某种形式的失败,这直接归因于其内部 IT 团队无法有效管理风险。安永调查的近 1200 名全球 C 级高管中有 87% 的人表示,他们需要增加 50% 的资金来应对日益增加的威胁形势。由于我们正面临技术和安全服务方面的全球技能短缺,这一问题更加复杂。这些问题直接影响组织维护和保留其信息技术以及现在的网络安全人员的能力。
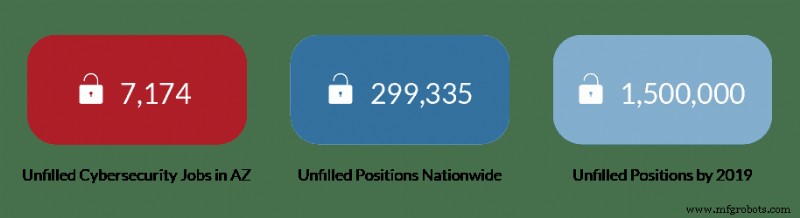
在业界为这种潜在的安全流行病做准备的同时,预测表明,大量安全服务提供商将会合并,同时更加关注和依赖自动化和机器学习工具。尽管公众担心,但这可能不是一件坏事。这些工具的日益复杂化、在许多方面执行分析和关联的能力以及自动化能力,可以提高我们的防御能力的效率或潜在的进步。
这一领域的行业领先供应商并没有袖手旁观。作为这样的供应商,phoenixNAP 处于从本地到国际的许多举措的最前沿。例如,至关重要的是,我们开始培养小到小学的孩子的知识,以获得对该领域的兴趣。我们与行业组织合作,赞助活动并在组织中发挥领导作用,以支持课程开发和意识。我们在威胁情报共享和使用不同的暗网数据源方面处于领先地位,以创建可用于早期威胁向量识别的预测分析。此外,我们与美国武装部队和美国退伍军人事务部合作,为有兴趣的军人提供途径,降低进入门槛,并拥有专门的支持系统,以便他们能够成功过渡到网络扮演平民角色。
“领导力”,我们将其视为我们的社会责任,以及我们对加强我们细分市场的安全态势的贡献。
为什么这与云中的安全性有关?
Gartner 2015 年的一项研究预测,年增长率为 16%。现实情况是,随着我们接近 2020 年大关,我们看到云服务上的 IT 支出增加了 32%。同一项研究发现,现在约有 40% 的 IT 预算用于云或 SaaS 相关服务。
从我们独特的角度来看安全的解决方案
可以安全地假设您已经在云中,或者您正在前往那里。我们的重点是教育我们认为安全云基础架构中最重要的组件,以及这些组件如何补充和支持现代企业的安全需求。正如路径-目标理论强调目标实现关系的重要性一样,作为技术服务提供商,我们相信与客户合作并加倍努力,成为产品创造和维持方面相互信任的顾问。云在您不远的将来。让我们为您保驾护航,一路指引您。
在phoenixNAP,我们有独特的视角。作为基础设施提供商,我们提供由互补工具和服务组成的服务组合,为组织提供全面、安全、基于云的解决方案。考虑到这一点,我们确定了中小型企业空间 (SMB) 的差距及其进入壁垒,以获取诸如此类的尖端技术。我们知道我们必须做什么:我们开发了工具来帮助这些企业获得世界一流的安全基于云的解决方案产品,满足并支持他们的监管需求。我们在性能、可恢复性、业务连续性、安全性以及现在的合规性方面设定了很高的标准。我们对中小型企业的热情和对安全的奉献是我们构建数据安全云的原因。我们的数据安全云旨在创建世界上最安全的云产品。
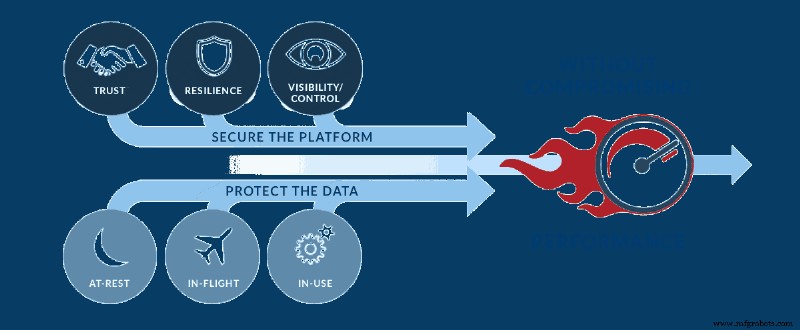
我们想要一种方法来构建一种解决方案,该解决方案将成为安全方面的黄金标准,而且每个人都可以完全访问。为此,我们需要将传统的咨询安全服务产品商品化,并以可承受的 OpEx 成本结构提供。这正是我们所做的。
云安全是一项共同的责任
2017 年云采用率调查发现,90.5% 的受访者认为云计算是 IT 的未来。多达 50.5% 的受访者仍然认为安全是一个问题。在这些担忧中,以下领域特别值得关注:
- 数据和应用程序集成挑战
- 监管合规挑战(54% 表示有 PCI 合规要求)
- 担心专有公共云平台会导致“锁定”
- 对大型云提供商的不信任
- 费用
考虑到这些观点,我们从头开始构建我们的解决方案。我们发现,我们需要监控、积极防御并为安全运营中心提供资源,以便对全球 24×7 的事件做出响应。我们设计了一个解决方案,我们与每个客户合作,共同分担保护环境的责任。最终,该策略有助于保护其后续客户的特权、财务、医疗保健和个人/人口数据的隐私和机密性。我们着手设计一个系统,帮助您实现安全态势的目标。
正如我们所看到的,我们面临的挑战是将云计算中的安全类型商品化并揭开神秘面纱。我们在集成工具方面投入了大量资源,并推动供应商从传统的资本支出成本模式转变为运营支出按增长付费的模式。最终,该策略实现了有利于该细分市场的定价结构并消除了任何进入壁垒,以便我们的客户可以使用以前为企业空间保留的相同工具和技术。
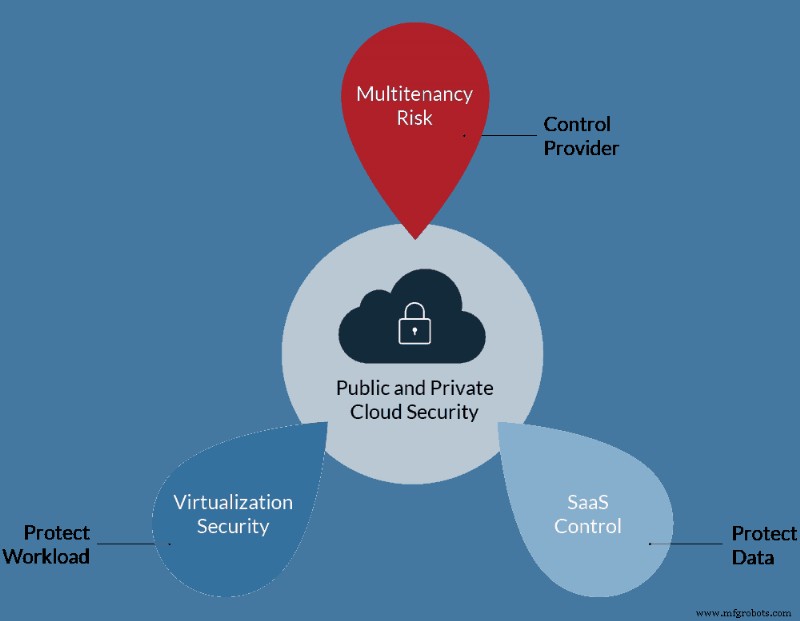
什么是云服务?
说到云服务,我们必须定义以下上下文:
私有云
- 私有云通常代表您内部的虚拟化解决方案,或者您或您的组织可能在数据中心托管中托管的虚拟化解决方案。
- 优化典型计算工作负载的空闲时间使用,通过将多个工作负载聚合到单个主机上,私有云将利用裸机管理程序平台固有的资源过度配置。
- 您拥有私有云。从技术上讲,它在您的设施中,在您的操作控制之下。因此,对安全控制的信心很高,但取决于操作员的技能和能力,以及他们保持适当安全卫生的能力。
- 不过,挑战在于您仍然需要采购和维护硬件、软件、许可、应急计划(备份和业务连续性),甚至是上述人力资源。包括组织无意中听到的持续开发和管理这些资源(培训、人力资源、医疗/牙科计划等)。
公共云
- 公共云是服务提供商为虚拟机、应用和/或存储等资源提供虚拟化基础架构的环境。这些资源通过互联网向公众开放。公共云通常是按使用付费模式运行的环境,客户只需为他们订阅和/或承诺的内容付费。
- 我们可以将公有云进一步分类为:
- 软件即服务 (SaaS)。 SaaS 的一个很好的例子是 Microsoft 的 Office 365。虽然您可以通过互联网浏览器本身使用很多工具,但您也可以下载面向客户端的软件,而所有实际工作都在云环境中进行。
- 平台即服务 (PaaS)。云提供商提供硬件和软件工具的解决方案,通常采用 OpEx 模型。
- 基础设施即服务 (IaaS)。当我们提到公共云时,这通常是大多数人所指的服务。一个典型的场景是当您访问一个网站并订购一个虚拟 Windows Server 时; X 数量的处理器、Y 数量的 RAM 和 Z 数量的存储。在phoenixNAP,我们提供这种服务。配置后,您安装 IIS 和 WordPress,上传您的网站,现在您的网站拥有面向 Internet 的服务器。被此模型吸引的消费者通常具有成本意识,并试图以最少的支出创建他们的解决方案。诸如面向 Internet 的防火墙之类的东西可能会被忽略或完全跳过。强大的系统架构实践,例如为 Web 平台和数据库/存储平台(带有内部防火墙)创建单独的工作负载也可能会受到影响。在这一点上可能显而易见的是,这是我们创建解决方案时重点关注的领域之一。
- 我们的价值主张是,这种类型的云平台减少了组织投资和维护其本地基础架构、资源甚至年度服务合同的需求。虽然这会减少资源需求,但不会消除它们。由于大多数许可费用要么通过提供商包括在内,而且很可能通过提供商的规模经济以显着降低的价格提供,因此您也可以保证获得一些可能的最优价格。
下表对比了转移成本分配模型:
传统 IT
资产成本
- 服务器硬件
- 存储硬件
- 网络硬件
- 软件许可
维护基础设施的劳动力成本
物理数据中心成本
- 电源
- 冷却
- 安全
- 保险
外包/咨询费用
通讯/网络成本
公共云
虚拟基础架构成本
- 服务器成本
- vProcs
- 虚拟内存
- vStorage
- 软件许可费用
- 专业服务
- 带宽成本
- 托管服务成本
混合云
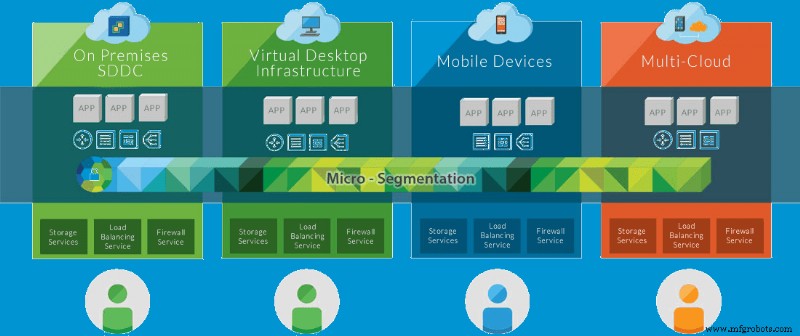
- 将混合云视为私有云和公共云的融合。期望的目标是让这两种环境中的工作负载相互通信,包括在两个平台之间无缝移动这些工作负载的能力。
- 虽然这在其他场景中也是可能的,但在混合云的情况下,通常会看到配置为内部部署环境的公共云环境。这种情况可能有适当的南北流量分段,在极少数情况下,由虚拟防火墙设备或最近基于 VMware NSX 的微分段技术促进适当的东西流量分段。
控制框架扮演什么角色?
控制框架是最佳实践的概述。一组强大且已定义的流程和控制,可帮助提供商遵守适当的安全状态。可以评估、审计和报告的状态,尤其是在符合审计流程验证的监管要求时。这对消费者来说意味着提供商已经构建了一个与行业一致的基于标准的解决方案。他们没有偷工减料,他们努力创造一种可靠且可互操作的优质产品,以应对您需要移植或移植基础设施组件的情况。提供商的基于标准的方法也可以用于满足您自己的法规遵从性需求,因为这可以解决您可以分配给提供商的清单中的组件。
与最优秀的人合作
市场份额数字是一种量化指标,尽管受阿尔法水平的影响,但在统计上仍然是合理的。英特尔和 VMware 显然是这一领域的领导者和全球创新者。在高要求的空间中集成组件以创建创新解决方案时,产品优势是一种定性衡量标准,是一项至关重要的资产。在phoenixNAP,我们为我们持续的合作伙伴关系感到自豪,并为与这些合作伙伴一起开发产品而感到自豪。我们相信联合品牌解决方案的价值,这些解决方案具有创新性,但由于其在该领域的长久性和领导地位而创建了稳定的平台。
在开发我们的数据安全云 (DSC) 产品时,我们很高兴使用最新一代的英特尔芯片组和早期发布的 VMware 产品代码。我们使用下一代工具和技术进行架构和实施,不受以前解决方案或方法的束缚。
我们将 VMware 的 vRealize Suite 和 vCloud Director 技术整合到一个世界级的解决方案中。在 phoenixNAP,我们不仅希望让我们的客户能够自行管理他们的运营任务,而且通过使用行业标准 VMware 作为平台,我们可以在他们的内部部署和数据安全云实施之间创建混合云解决方案。
重新开始
由于我们想设计一个安全的云服务产品,我们选择不受传统的影响。从基于软件定义网络的全新网络平台开始,我们创建并构建了一个灵活、可扩展的解决方案,并结合了微分段和数据隔离最佳实践。我们在整个虚拟化平台堆栈和互连通信结构中设计了这种级别的灵活性和控制力。
设计方法
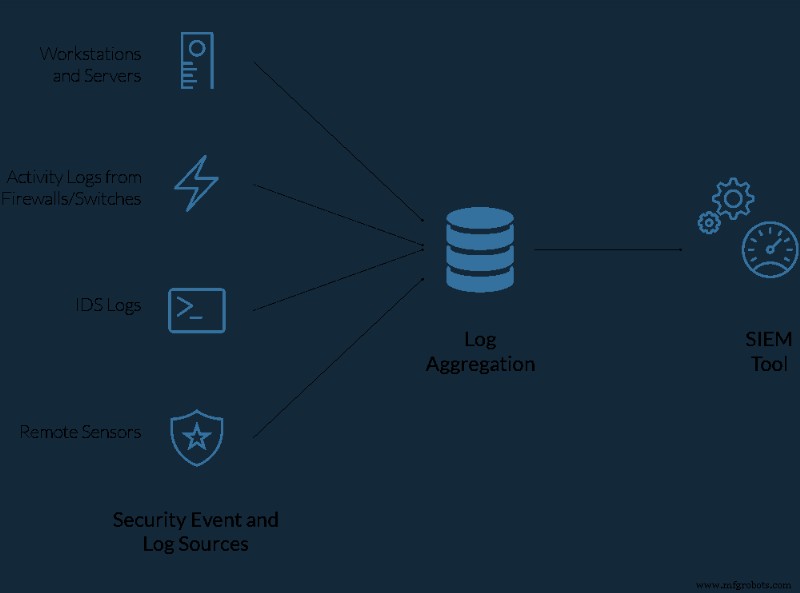
我们利用我们在实现合规目标方面的广泛背景;采用框架方法,使用行业最佳实践,预测获得行业和合规性认证(如 PCI、HIPAA 合规性和 ISO 27002(即将推出))所继承的需求和限制。我们设计了一个灵活且安全的架构,辅以 VMware LogInsight 日志收集和聚合平台,将与安全相关的事件流式传输到 LogRhythm SIEM,并由我们的 24×7 安全运营中心 (SOC) 监控。
我们证明了这一点
有什么比让最受尊敬的组织验证和认证我们更好的方式来证明我们在安全标准中实现了我们的目标。我们让 TrustedSec 评估了我们的环境,并让他们证明它符合他们的期望。然而,我们并没有止步于仅仅实现合规性。此外,作为安全专家,我们审核了我们的环境,超出了监管标准。我们将框架设计为采用“不妥协的方法”,以及从技术和安全角度“做正确的事”的基本理念。经我们对该安全云平台的 PCI 认证证明。
推出我们的安全服务产品
经过多年的广泛测试和客户的反馈,我们将安全风险管理和事件响应能力构建为一项服务产品,可供我们的整个客户群使用。我们通过集成先进的安全编排和自动化测试工具以及与公共和私人信息共享与协作 (ISAC) 组织建立战略伙伴关系来增强我们的安全运营。通过我们从我们自己的系统、成员组织和暗网实时收集全球威胁向量数据的能力得到增强,我们利用独特的丰富技术,对这个社会的社会结构进行预测分析;目标是创建可操作的情报或预警系统,以支持我们的防御态势。
这意味着我们正在构建高级工具,以便在威胁影响您的业务之前对其进行检测。我们正在使用这些工具采取预防措施来保护我们监督下的客户网络。可能会看到最新威胁的行为会从您身边溜走,而不会将您包括在内。
创建安全云基础架构的分层方法

经过验证的基础
phoenixNAP 在设计、开发和运营创新的基础设施解决方案方面拥有悠久且久经考验的历史。作为一家金融交易领域的母公司,我们在这些关键解决方案的安全操作方面拥有广泛的知识和专业知识。作为全球数据中心设施的运营商,我们建立了值得信赖的声誉和运营流程,以支持我们多样化和庞大客户群的需求。
我们的 SOC-1、SOC-2 和 SOC-3 认证为物理和逻辑访问控制、数据安全以及业务连续性管理和程序建立了基准。我们的 II 类名称在实践中验证了这些能力。我们的 PCI-DSS 认证确立了我们对“做正确的事”的承诺和信誉,以创造一个体现您对最高级别安全状况的关注的环境。
冗余全局通信结构
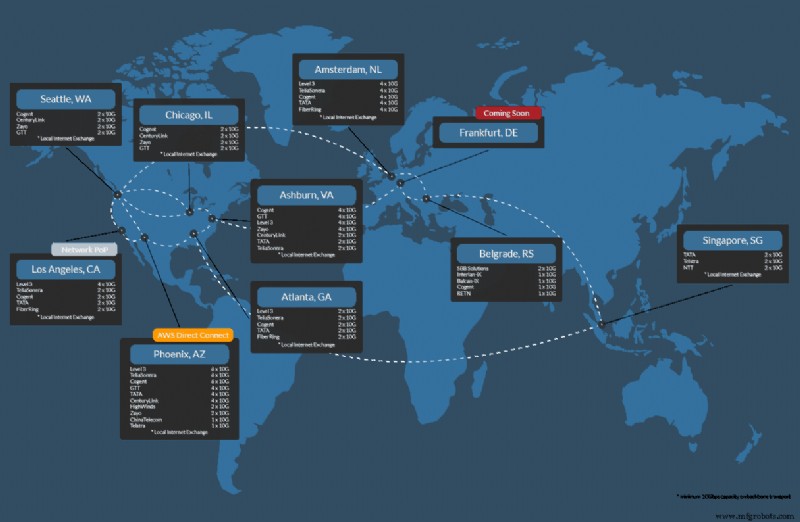
在phoenixNAP,我们相信每位客户都应该得到最高形式的安全和保护。在我们最消费者层面,我们的客户受益于基于六职业混合连接的互联网服务,以及内置于通信结构中的 DDoS 缓解等技术。我们的每一位客户都获得了这种开箱即用的卓越保护水平。借助我们的数据中心可用性专业知识,我们设计了一种网状交换结构,它具有快速弹性,消除了单点故障,让我们有信心提供 100% 的服务水平可用性 (SLA) 保证。
高度可扩展的硬件平台
Lisa Spellman - 英特尔至强和数据中心副总裁/总经理
基金会的安全
- 信任根模块 (TPM)
- 用于验证的内置指令集(Intel TXT)
- 快速、高质量的随机数生成器 (RDSEED)
- 固件保证 (BIOS Guard)
内置生态系统
- 高效配置和初始化(英特尔 PTE)
- Scalable management with policy enforcement (Intel CIT)
- Direct integration with HyTrust and VMware, etc.
A New Level of Trust
- Secure, Enterprise Key Management
- Trusted connectivity
- Remote attestation fo the secure platform
- Compliance and measurement at the core
Designed around the latest Intel Xeon processor technology alongside our extensive expertise in managing highly scalable workloads in our other cloud offerings, we built a computing platform that achieved 1.59X performance gaines over previous generations. These increases that are passed down into our customer’s workloads, providing them with better performance, and a higher density environment to optimize their existing investment, without any capital outlay; in most cases without any additional OpEx commitments.
Advanced Hypervisor Technology
We build a foundational commitment to VMware, and our commitment to integrate the latest tools and techniques to empower our customers to do what they need, whenever they need it.
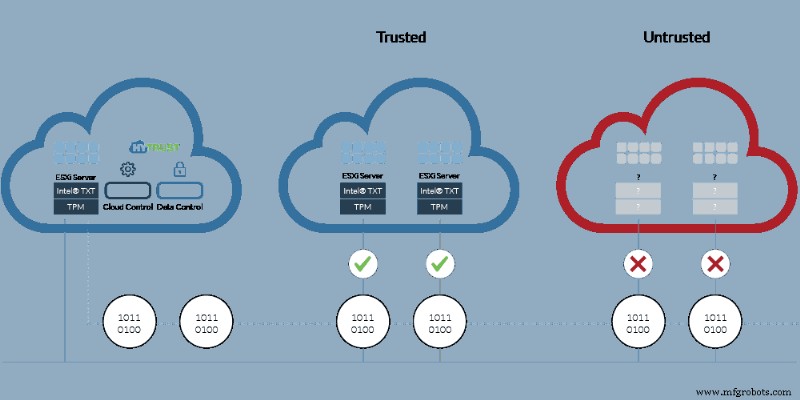
Using Hybrid Cloud Extender we can help customers bridge the network gaps to hosted cloud services while maintaining network access and control. Tools like VMWareNSX allow for the creation of logical security policies that can be applied to a Virtual Machine regardless of location (cloud or on-premise). The integration of the latest Intel Cloud Integrity Toolkit allows for platform security with unmatched data protection and compliance capabilities.
Our vRealize Suite and vCloud Director integration is no different. We provide our customers with direct access to the tools they need to manage and protect their hybrid cloud environments effectively. In the event the customer wishes to engage phoenixNAP to perform some of these tasks, we offer Managed Services through our NOC and 3rd party support network.
Segmented Components
Experience has taught us how to identify and prevent repeat mistakes, even those made by strategic or competitive partners in the industry segment. One of those lessons learned is the best practice to section and separate the “Management” compute platform, from the “User compute platform.” Segmentation will significantly minimize the impact of a “support system” crash, or even a heavy operational workload, from impacting the entire computing environment. By creating flexible and innovative opportunities, we train our teams to reflect, communicate and enhance their experiences, creating a knowledgeable and savvy operator who can step onto the batter’s box ready to do what’s asked of them.
Threat Management
We believe that we have created a state-of-the-art infrastructure solution with world-class security and functionality. However, the solution is still dependent on a human operator. One, that based on skill or training, could be the weakest link. We, therefore, engage in continuous education, primarily through our various industry engagements and leadership efforts. This service offering is designed to be a high touch environment, using a zero-trust methodology. A customer, who is unable to deal with the elements of an incident, can see us engage on their behalf and resolve the contention.
If all else fails, and the environment is breached, we rely on 3rd party pre-contracted Incident Responders that deploy in a rapid format. The proper handling of cybersecurity Incident Response requires a Crisis Communication component. One or more individuals trained in handling the details of the situation, interfacing with the public and law enforcement, and based in the concepts of psychology, are trained to be sensitive and supportive to the various victim groups of the situation.
As we bundle backup and recovery as a core service in our offerings, we can make service restoration decisions based on the risk of overwriting data vs. extended downtime. Using the cloud environment to our advantage, we can isolate systems, and deploy parallel systems to restore the service, while preserving the impacted server for further forensic analysis by law enforcement.
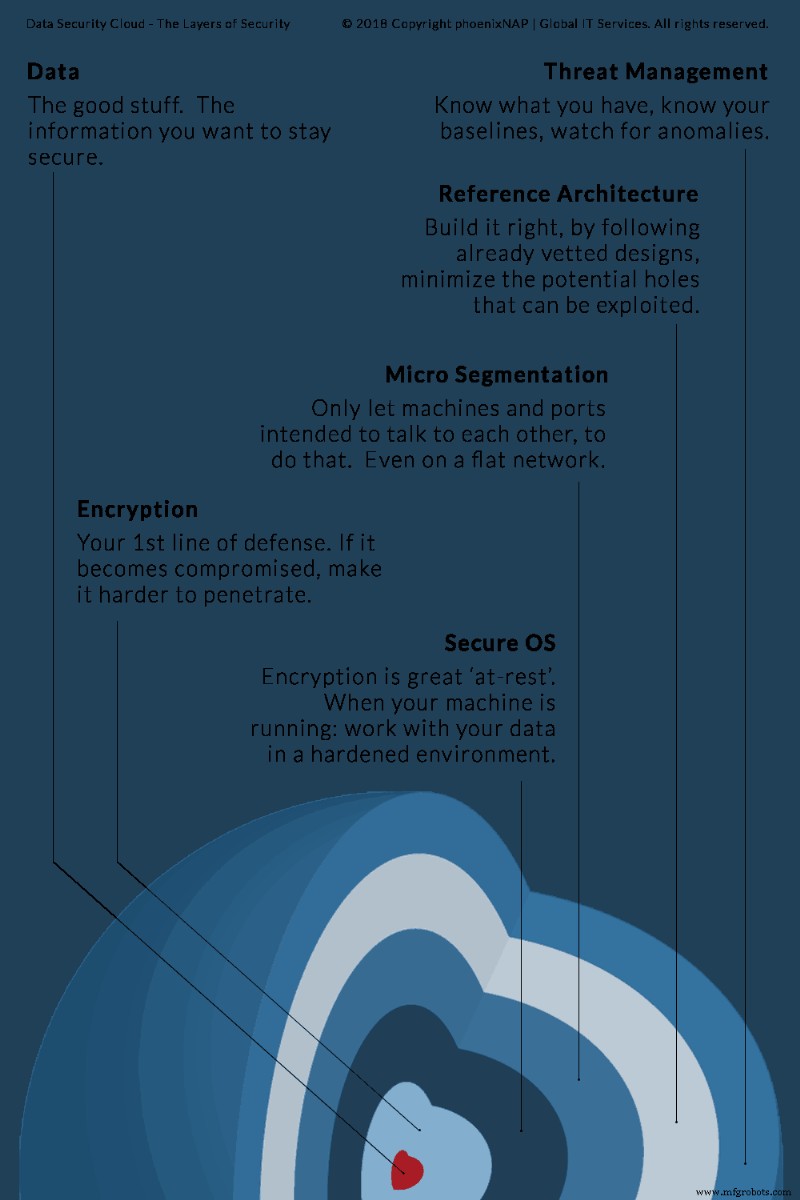
It’s All About the Layers
Hierarchy of Virtual Environment Security Technologies
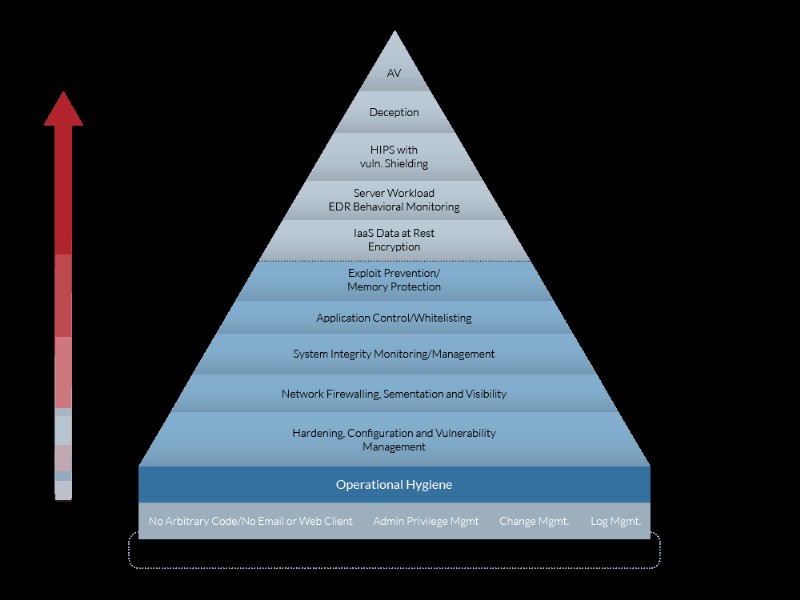
Security solutions are designed to defend through depth. If one layer is compromised, the defense process begins by escalating the tools and techniques to the next tier. We believe that a layered approach as described creates a secure and stable solution that can easily be scaled laterally as the needs and customer base grows.
Why Does This All Matter?
In one of his articles in the CISO Playbook series, Steve Riley challenges IT leaders not to worry that migration to the cloud may require relinquishing total control but encourages them to embrace a new mindset. This mindset is focused on identity management, data protection, and workload performance.
The primary is likely a reference to the cost savings achieved from consolidation, and transfer of responsibility to a service provider.
- Converting CapEx expenditure to OpEx ones can surely improve cash flow to those in the SMB market space.
- Reducing technical overhead through the elimination of roles no longer required, can provide far more operating capital, and
by re-focusing core-resources to concentrate on core-competencies, create business advantages in the areas that are important to the organization.
According to Gartner, the benefits of cloud migration include the following:
- Shorter project times:Cloud IaaS is a strong approach for trial and error, offering the speed required to test the business model success.
- Broader geographic distribution:The global distribution of cloud IaaS enables applications to be deployed to other regions quickly.
- Agility and scalability:The resource is pay-as-you-go. If an application is designed correctly, then it is simple to scale the capability in a short period.
- Increased application availability:As described, we have demonstrated the highest levels of security and reliability. If you have the right application design, you can develop application availability accordingly.
What’s Fueling the Cloud-First Strategy?
We hear many organizations adopting a cloud-first strategy, where they default to a cloud-based solution, until it proves unable, or not feasible before they consider other options. Factors driving this trend include:
- Reduced infrastructure and operational costs. From a reduction in capital expenditures, using the elasticity of cloud services, lower overall software costs and potential reduction of IT staff, organizations report approximately 14% in savings.
- Flexibility and scalability to support business agility. Agility is defined by the ability to bring new solutions to market quickly. The ability to control costs, leverage different types of services, and being flexible to adapt to market conditions.
- Cloud services tend to use the latest in innovation. Being able to leverage the high rate of innovation in this space, an organization can benefit by incorporating it as part of their business strategy.
- A cloud-first strategy can drive business growth through a supportive ecosystem.
Things to Consider
Not every workload is appropriate or destined for cloud-based compute platforms. The scoping part of any cloud migration project should start by identifying and selecting workloads that are easily migrated and implemented in multi-tenant cloud implementation.
The customer needs to understand the profile and characteristics of their workloads. For many years we would have never considered moving database workloads off of physical hardware. This is a similar case where high I/O or hardware timer reliant workloads (such as GPS or real-time event processing) may be sensitive to being in a shared, multi-tenant computer environment.
- More importantly, cloud services predominately revolve around x86-based server platforms. Therefore, workloads that are reliant on other processor architecture, or even specialized secondary processing units or even dongles, do not make ideal cloud candidates.
In contrast, cloud-based infrastructure allows for:
- Business Agility – for rapid deployment, and even rapid transition from one platform to another, with low transition costs.
- Device Choice – The flexibility to deploy, tear down, and redeploy various device configurations in a matter of clicks.
- Collaboration – Cloud providers typically provide an expert-level helpdesk, with direct access to a community of experts that can support your needs.
There are many reasons to consider a hybrid strategy where you combine workloads. What needs to stay on bare-metal can remain on bare metal servers, either in your facility or a colocation facility such as ours, while staying connected to the cloud platform via a cross-connect, gaining the benefits of both scenarios.
Cloud computing security consists of a broad set of concerns. It is not limited to data confidentiality alone, but concerns for privacy, regulatory compliance, continuity and recovery, and even vendor viability. Staying secure in the cloud is, however, a “shared responsibility.” It requires partnerships, especially between the customer and their infrastructure service provider. Nobody needs to be convinced that data breaches are frequent, and often due to management or operator neglect. Customers are becoming tired of their data being disclosed and then used against them. Most recently, abused via an email-based threat vector, where the bad actor quotes a breached user ID and password, as a way to convince the target recipient to perform an undesired action, behind the mask of perceived authenticity.
Any organization that accepts Personally Identifiable Information (PII) of its customer base establishes with that customer, an implied social contract to protect that information. At phoenixNAP, we have demonstrated leadership in the infrastructure space on a global scale, through partnerships with customers, solution aggregators, and resellers. We have created innovative solutions to meet the unique challenges faced by businesses, going above and beyond to achieve the goals desired by the target organization.
Notes from the Author:Elements of a Strong Security Strategy
Over the years, I have learned many important lessons when it comes to creating solutions that are secure and reliable. Here are some final thoughts to ponder.
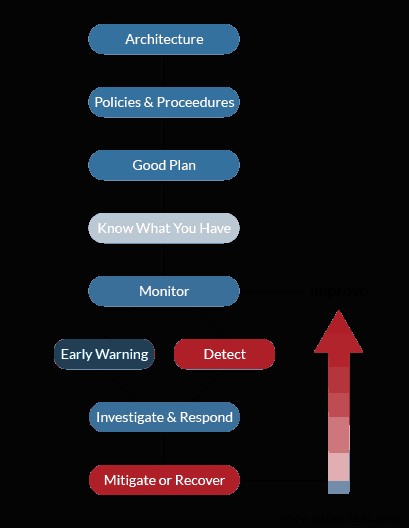
- There is no substitute for strong architecture. Get it right and you have a stable foundation to build upon. Get it wrong and you will play whack-a-mole for the rest of that life-cycle.
- Have detailed documentation. Implement policies and procedures that make sense. Documentation that supports the business process. Security policies for the cloud cannot burden the users. If they do, they just become a target for shadow IT. The policy needs to be supportive of the existing process while implementing the control it absolutely needs. A little control is better than no control due to a workaround.
- Plan for a breach, plan to be down, plan for an alien invasion. If you plan for it, you won’t be caught in a state of panic when something undoubtedly happens. The more off-the-beaten-path a scenario seems, the better you can adopt for when real-life scenarios arise.
- You can’t protect what you don’t know you have. Asset management is the best thing you can do for your security posture. If it’s meant to be there:document it. If it’s not meant to be there:make certain that you have a mechanism to detect and isolate it. Even to find out who put it there, why and when.
- Now that you know what you have:monitor it. Get to know what normal behavior is. Get to know its “baseline.”
- Use that baseline as a comparative gauge to detect anomalies. Is this system showing inconsistent behavior?
- Investigate. Have the capability to see the alert triggered by that inconsistent behavior. Are you a 24/7 operation? Can you afford to ignore that indicator until the morning? Will your stakeholders, including your customers accept your ability to detect and respond to the Service Level Agreement (SLA) you extend to them? Can you support the resourcing needed for a 24/7 operation, or do you need to outsource the Threat Management component at least in a coverage extension model? The best SIEM tools are useless without someone actioning the alerts as soon as they pop up. Machine learning helps, however, it cannot yet replace the operator.
- Mitigate the problem or be able to recover the environment. Understand what your Recovery Point Objectives (RPOs) and your Recovery Time Objectives (RTO). Do your current solutions meet those goals? Can those same goals be met if you have to recover into a facility across the country, with no availability from your current staff due to the crisis being faced? How will you communicate with your customers? Do you have a crisis communicator and incident handler as part of the response team?
- Take your lessons learned, improve the process and do it all over again.
No single vendor can provide you with a “silver bullet.” Any vendor that tells you such, is someone you should shy away from. Every customer’s needs are unique. Each situation takes a unique blend of solutions to be effective. Hence your vast network of partner relationships, to provide you with the solutions you need, without trying to make you fit onto one of their offerings.
The offer is always on the table. At phoenixNAP, we will gladly take the call to discuss your concerns in this area, and provide advice on what our thoughts are on the topic of interest. Promoting and supporting properly secured environments is part of our social responsibility. It is part of our DNA and the core philosophy for building products in this segment. Let us be your partner in this journey.
Use of Reference Architectures
One of the benefits of a cloud-based, secure infrastructure such as our Data Security Cloud, is the ability to implement battle tested reference architectures that in some cases go above and beyond the standard capabilities of what’s possible in the physical environment.
In what we would consider an extreme case; an architecture as depicted above creates multiple layers of security with various gateways to get to the prized databases that most bad actors are after. Let’s not ignore the bad actors that want to take control of the web infrastructure to infect visitors with infectious payloads; however, the real prize sits inside those databases in the form of PII, PHI, or PCI data. While the various levels of defensive components are designed to make it difficult for the bad actors to storm the castle, the 24×7 Threat Monitoring will undoubtedly catch the multiple attempts and anomalous behavior, triggering an investigation and response activity.
Through a robust combination of tools, technology, services, and a cost model that’s supportive of the needs of the SMB space, we believe we have demonstrated our leadership, but more importantly, we have created a solution that will benefit you; our SMB customer. We aim to have created a complete security solution that you can take forward as you further define your cloud strategy.
Our Promise
We have assembled a world-class team of highly experienced and skilled leaders, who are passionate about cloud security. As global thought leaders, we design for the world and implement locally. We create sustainable solutions, understanding a customer’s appetite and limited budget. Let us show you how we can benefit your goals through our solutions offerings. Keeping with our promise to “do the right thing” as it involves finding the best solution for you.
Get Started with Data Security in Cloud Computing Today; Contact phoenixNAP today.
云计算


